Heimdal Security published an interesting post on the increase in malicious scripts that are being injected into legit websites in order to serve ransomware.
Heimdal Security recently published an interesting blog post on the increase in malicious scripts that are being injected into legit websites in order to serve malware. The attackers compromise websites running an outdated content management system (CMS) and deploy popular the Neutrino exploit kit.
The statistics confirm that crooks mainly compromise WordPress websites, in August experts from security company Zscaler uncovered a malware campaign which relies on thousands of hijacked WordPress sites hosting the Neutrino Exploit Kit.
According with statics provided by w3techs.com
“WordPress is used by 58.8% of all the websites whose content management system we know. This is 24.4% of all websites.”
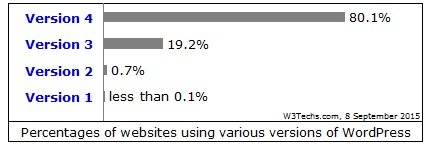
This means, roughly 1 billion legit websites are vulnerable to this kind of attacks, if we go deeper by dividing the WordPress websites by versions we will have the following situations:
Be aware, even WordPress instances running outdated plugins or with poor security settings could be potentially compromised.
We are dealing with huge numbers here, it has been estimated that 409 million people read WordPress Blogs per month, and from those, 142 million legit websites can be exploited.
Injection Script, the available data
The analysis performed by Heimdal concludes that the malicious script is injected in the website references, “a halfway house” to the domain: thedancingbutterfly [.] Com.
Then the domain thedancingbutterfly.com redirects the traffic to a Neutrino exploit Kit and tries to deliver to the victim’s PC the Teslacrypt ransomware.
Neutrino will try to exploit Adobe Flash player/ Internet explorer / Acrobat vulnerabilities in order to compromise the machine and download further malicious payloads.
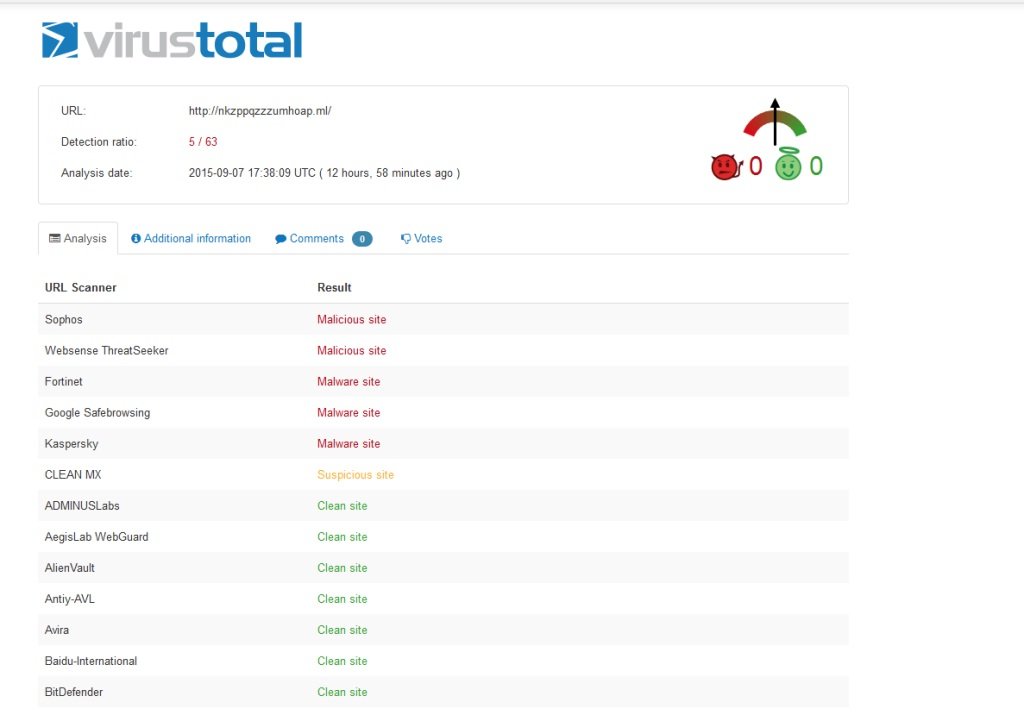
All the vulnerabilities have low detection rates (in Virustotal), and even the domain used for the script injection to redirect victims, ” nkzppqzzzumhoap [.] Ml” doesn’t have a good detection rate:
“The domain is delivered through its own name server ns1 and root, and is hosted in Netherlands by OpenTLD BV. The same server contains other toxic domains used in attacks that employ the Neutrino exploit kit.” states the post.
Teslacrypt has also a low dection rate, current being 10/56. About the Teslacrypt, we know that encrypts many extensions (normally the most important ones), recent versions also target gaming data.
After the encryption of the users’ files, the Teslacrypt drops for each folder something like:
- restore_files_ [4 random letters] .txt
- restore_files_ [4 random letters] .html
The files, of course, contain the information on how to buy the decryption key.
Teslacrypt will also delete the shadow copy on the local drive using the command:
“C: \ WINDOWS \ system32 \ vssadmin.exe” delete shadows / all / Quiet “
Teslacrypt will inject itself into “iexplore.exe” and “cmd.exe”.process.
This ransomware will also “call a friend”, an info stealer belonging to the Pony family using the domain ” light-tech [.] Pl.”
Please, if you own a website, and you manage it, always keep in mind the importance to update and patch it, this is the only way to avoid problems to you and millions internet users.
About the Author Elsio Pinto

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.