Vulnerability is easy to exploit, hard to spot. A CSRF vulnerability existed in the core of the Yandex Browser that allowed attackers to trick the browser’s synchronization feature into sending the user’s browsing data to the wrong account.
If exploited, the vulnerability would have allowed an attacker to steal the victim’s passwords, browser history, bookmarks, and autocomplete info, the usual data that’s synced between devices via this feature.
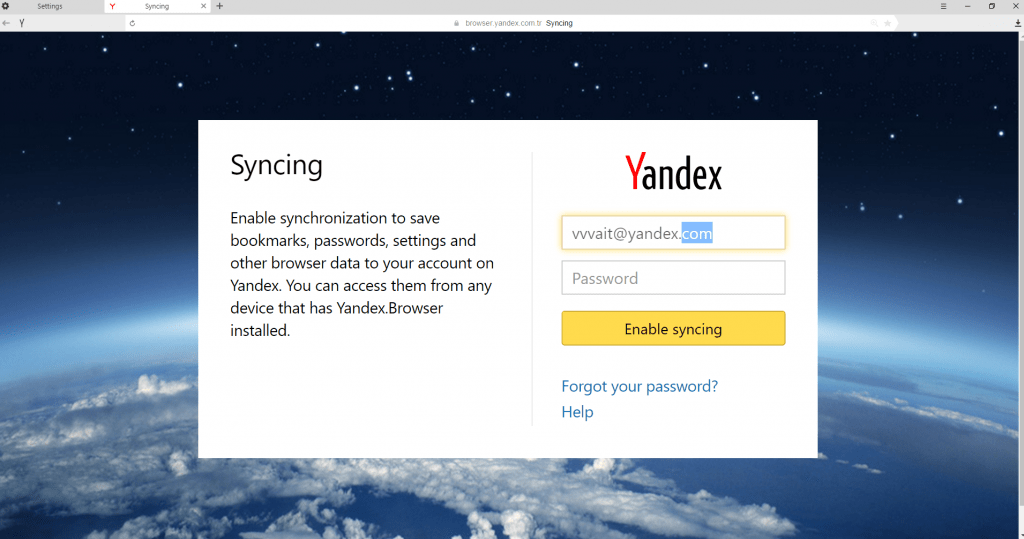
Vulnerability affected Yandex Browser’s data sync feature
The vulnerability per se existed in the Yandex Browser login form, where users enter the email account and password they used to create a profile inside the browser.
The functionality is similar to Chrome’s data synchronization feature. The Yandex Browser is built on Chromium, the open source browser engine also used by Chrome.
Softpedia has reached out to Ziyahan Albeniz, the Netsparker researcher who discovered this flaw, to inquire if it also affects Chrome’s sync feature, but common sense dictates it probably doesn’t, due to different codebases that handle authentication procedures in Google’s browser.
Vulnerability is easy to exploit via malicious web pages
According to Albeniz’s report, the bug is trivial to exploit. An attacker only needs to trick a user into accessing a malicious website.
This website will include code that creates a Yandex Browser data sync login form and submits the data with the attacker’s credentials.
The CSRF bug will allow this information to take hold and start an automatic syncing operation that sends a copy of the user’s data to the attacker.
“Note that unless the victim finds out what is happening the browser will keep on syncing data to the attacker’s account, therefore things such as new credentials and bookmarks will be synced to the attacker’s account without the victim’s knowledge,” Albeniz explains.
The researcher informed Yandex of the issue on December 17, 2016. Disclosing the bug and getting it fixed was a little tricky, with minimal communication from Yandex, the company not even bothering to tell the researcher they fixed the issue in May 2016. Below is the full disclosure timeline.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.